Discover how data protection federation streamlines security in document collaboration platforms like SharePoint and Nextcloud. Learn about federated security and access, improved data governance, and reduced risks to ensure efficient, secure, and seamless management of sensitive information.
1. What is Federated Security?
Federated security is an IT security methodology that allows centralized authentication and authorization to be applied across multiple, interconnected systems or organizations. It provides a way to ensure seamless integration and interoperability between various platforms while maintaining robust access control. Instead of managing separate credentials for each system, federated security enables users to authenticate once and gain access to multiple resources, reducing complexity and enhancing security.
A key concept within federated security is federated identity, which is the foundation of this approach. Federated identity is a trusted connection between identity providers (IdPs) and service providers (SPs). Here, user credentials are managed by a central identity provider, and other interconnected systems trust this provider to authenticate users. This trust framework ensures that a user’s identity is consistently recognized across different platforms. If you would like to learn more, here is an article from Microsoft.
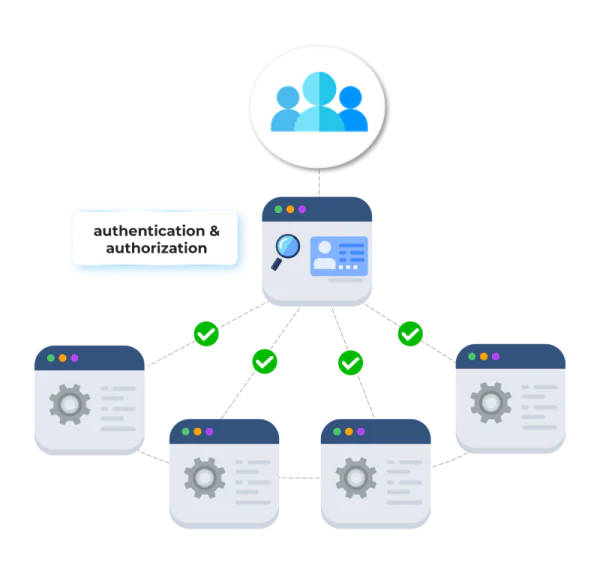
A typical federated security architecture consists of:
- 1. Identity Providers (IdPs): These manage user authentication and identity verification.
- 2. Service Providers (SPs): These are the systems or applications that rely on the IdP to validate user access.
- 3. Federation Protocols: Technologies like SAML (Security Assertion Markup Language) or OAuth that enable secure communication and information exchange between IdPs and SPs.
- 4. Policies and Agreements: Predefined security policies and trust agreements that outline roles, permissions, and access rules between entities.
This architecture simplifies access management, enhances user experience, and ensures security policies are uniformly enforced across diverse platforms. Federated security not only reduces administrative workloads but also mitigates risks associated with fragmented systems and multiple access credentials.
2. And Federated Access?
Federated access extends the principle of federated identity into the realm of IT security by focusing specifically on how access to resources and applications is managed across multiple systems. It is a method where access rights and privileges are centralized yet seamlessly extended to various interconnected environments or systems. This approach not only simplifies the user experience but also streamlines the management of access permissions.
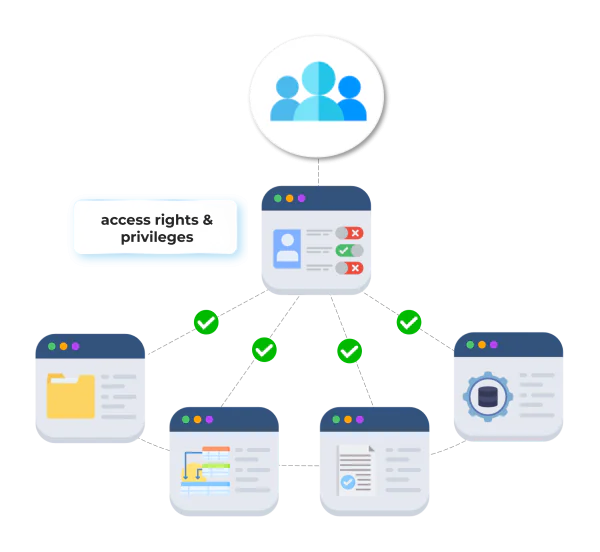
In a federated access environment, the link between identity providers and service providers ensures that access policies are consistent and uniformly applied. This simplifies administrative processes and reduces the risk of unauthorized access, as users’ permissions are centrally managed rather than being scattered and duplicated across disparate systems.
Federated access plays a crucial role in enhancing security and operational efficiency by ensuring that access controls are aligned with the organization’s overall security policies and business needs. This approach not only boosts security but also supports compliance with regulatory requirements, making it a vital component of modern IT security strategies.
3. Why is Federated Security Important in Cybersecurity?
Federated security is essential in cybersecurity because it simplifies access management while strengthening protection against data breaches and unauthorized access. By centralizing authentication and extending secure access controls across systems, organizations can ensure consistent enforcement of security policies. This approach reduces human errors, eliminates redundant tools, and addresses key risks associated with fragmented security practices.
Key benefits include:
- 1. Enhanced Data Protection: Federated security ensures sensitive information remains secured through unified access management.
- 2. Operational Efficiency: IT teams spend less time managing individual credentials and permissions across systems.
- 3. Improved User Experience: Single sign-on (SSO) eliminates the need for multiple passwords, making workflows smoother and reducing credential fatigue.
- 4. Regulatory Compliance: Simplified auditing of access controls ensures alignment with industry regulations like DORA or NIS2.
Consider the cloud-based collaboration tools used in large organizations, such as Google Workspace or Microsoft 365. Without federated security, employees would require separate credentials for each service, increasing the risk of weak passwords and inconsistent access control. With federated security, organizations integrate these platforms under a trusted identity provider, ensuring employees can securely access multiple tools or data through SSO.
Overall, federated security delivers a cohesive strategy to safeguard organizational resources while improving efficiency.
4. Real-World Examples of Federated Practices
Federated security is increasingly adopted across various sectors, from industry to finance and public administration, reflecting its versatility and effectiveness. Let’s explore two real-world examples and understand how different types of federated security systems are applied.
1. Industry: Manufacturing
In the manufacturing sector, federated identity management systems streamline access to shared resources across multiple plants and partners. By adopting Single Sign-On (SSO), employees can access a range of tools from CAD software to supply chain management platforms without logging in separately for each one. This integration not only enhances productivity but also ensures stringent security protocols are consistently applied, preventing unauthorized access across the vast industrial network. Learn more about data protection in the supply chain here.
2. Financial Company: Banking Sector
Financial institutions are particularly sensitive to security breaches. A large bank might employ Federated Identity as a Service (IDaaS) to manage customer access across digital banking services, investment platforms, and partner financial services. This federated system enhances user convenience by allowing seamless transitions between services, while also safeguarding sensitive financial data through a centralized, secure authentication process. The bank can thus offer robust customer experiences without compromising security standards.
5. How does federated access help with data permission management?
Federated access plays a pivotal role in permission management by offering a centralized approach to controlling and monitoring data access across multiple systems. In today’s interconnected digital ecosystems, ensuring secure and efficient permission management is critical for preventing unauthorized data access and minimizing the risks of breaches.
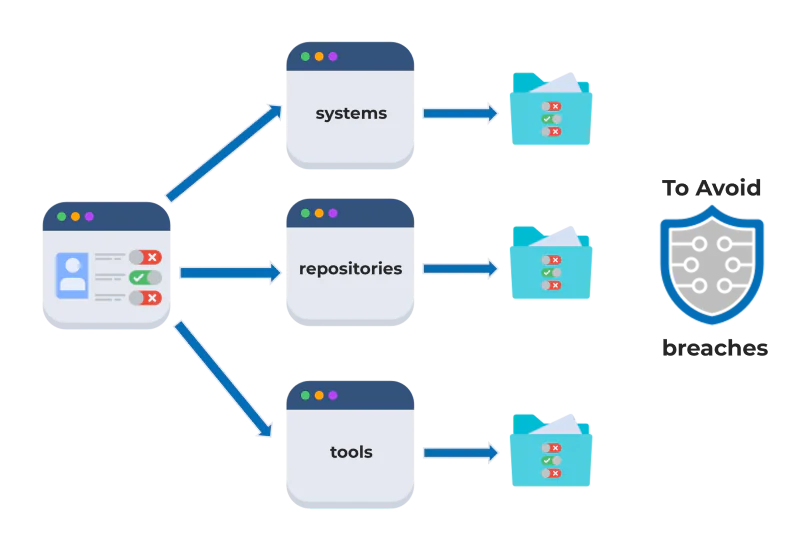
Here’s how federated access enhances permission management:
1. Centralized Authorization Control
Federated access enables organizations to unify permission management under a single framework, rather than managing individual systems independently. This centralization improves consistency in enforcing access policies and reduces the complexity associated with fragmented security protocols.
- Administrators can define roles, attributes, and permissions in one place, with those policies automatically reflected across all connected systems.
- This strengthens governance, as organizations gain a clear overview of “who has access to what” across all platforms.
2. Granular Access Management
Federated systems often leverage attribute-based access control (ABAC) or role-based access control (RBAC) principles, know more here. These models allow permission levels to adapt dynamically based on a user’s role, location, or specific attributes.
For example: A healthcare worker may access specific patient data during working hours but have restricted permissions outside of those hours. Federated access ensures permissions align with organizational policies while preventing excessive or unnecessary data access.
3. Scalability Across Complex Environments
As organizations grow, managing permissions across multiple databases, cloud services, and applications can become overwhelming. Federated access scales with expansion, ensuring robust permission management across diverse infrastructures, whether they include remote teams, external partners, or multi-cloud environments.
4. Reduced Risk of Human Error
Manual permission management often leads to mistakes, such as granting incorrect access levels or forgetting to remove permissions after an employee leaves. Federated access automates these processes, reducing vulnerabilities caused by human error and improving overall security hygiene.
Federated access provides a unified framework for managing permissions to data stored across diverse platforms such as storage repositories (e.g., SharePoint) and data security solutions like Enterprise Digital Rights Management (EDRM). By aligning access controls across these systems, federated access ensures that sensitive information is consistently protected, regardless of where it resides. Remember that it is also important to protect data in all three states, not just rely on access measures.
This approach eliminates silos by linking permission policies to a centralized identity, enabling organizations to apply uniform security protocols across file storage, document management, and collaboration tools. The result is a more cohesive, scalable, and secure method for controlling data access in increasingly complex environments.
6. Introducing SealPath´s Federated Policies for SharePoint and Nextcloud
SealPath’s Federated Policies offer a seamless and dynamic approach to protecting sensitive data stored in platforms like SharePoint and Nextcloud. By automatically applying protection to a root folder and its contents, these policies ensure that access permissions are continuously synchronized with the folder’s permission settings. This integration removes the need for manual updates, providing robust security that adapts in real-time to changes in user permissions.
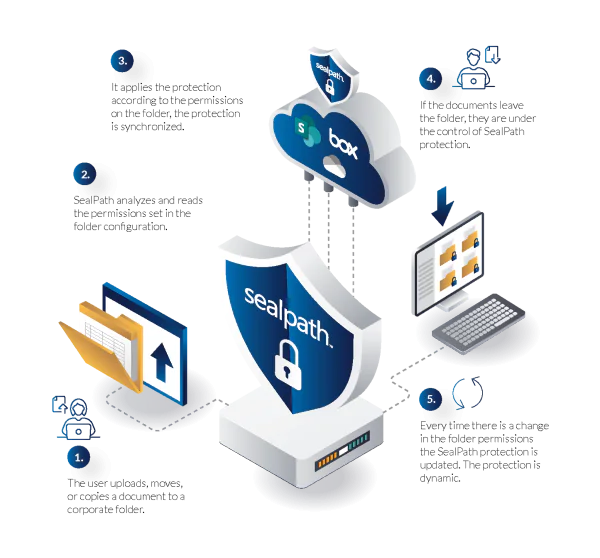
Automatic Protection: SealPath federated rules automatically apply protection to designated root folders and their files, ensuring consistent security.
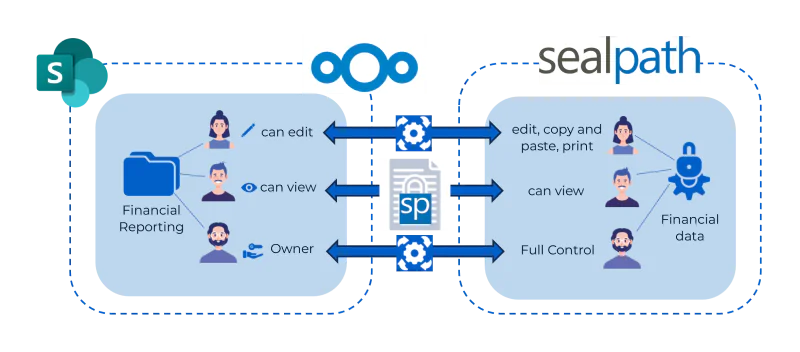
Dynamic Synchronization: Permissions within SealPath federated policies mirror the user permissions assigned to the folder. For example, an employee with edit permissions for a SharePoint folder (e.g., Financial Reportings) is granted equivalent edit permissions for the protected documents within that folder.
Granular Control: User permissions are determined exclusively based on the folder’s access rules and are managed via the SealPath web administration console. These permissions are non-editable by users, ensuring centralized control.
Folder-Specific Protection: Federated policies apply only to the defined folder and its contents, cannot be associated with other folders, and cannot be used to protect individual files outside the defined scope.
Real-Time Detection of Changes: SealPath reads folder permissions continuously and adapts protection settings immediately upon detecting changes. This ensures evolving permissions (e.g., promotions or role changes) are reflected in real-time.
Flexible Permission Equivalence: Organizations can customize how folder permissions translate to SealPath policy access levels.
For example:
Read in SharePoint → View permission in SealPath policy.
Write in SharePoint → Edit, copy, paste, and print permissions in SealPath policy.
Owner in SharePoint → Full control in SealPath policy.
Security Beyond the Folder: Even if documents leave the protected folder, they remain under SealPath control ensuring continued protection and mitigating the risks of unauthorized access or data leakage.
SealPath’s Federated Policies create a powerful synchronization mechanism between folder permissions and document security, providing organizations with automated, scalable, and airtight protection for sensitive files stored in SharePoint and Nextcloud.
7. Advantages and Benefits of Using SealPath Federated Policies
SealPath’s Federated Policies introduce a highly efficient and automated approach to securing sensitive data across platforms like SharePoint and Nextcloud. By aligning security measures with folder permissions, organizations can achieve dynamic protection without the complexity of manual intervention.
1. Aligned Data Security Measures
SealPath federated policies ensure that data protection is always in sync with folder access permissions, promoting a uniform approach to security across the organization.
2. Consistent Data Access Policies
Federated policies eliminate inconsistencies in access control, ensuring all users have permissions that align with their roles, improving transparency and trust.
3. Improved Data Governance
By applying uniform controls across folders, SealPath federated policies enhance data governance, reducing the risk of misconfigured rules or permissions that could lead to security vulnerabilities or operational friction.
4. Centralized Access Control
Permissions and rules are managed directly from the SealPath web administration console, simplifying access control management and eliminating the need for individual file-level adjustments.
5. Real-Time Application of Policies
Protection is applied instantaneously based on predefined rules, adapting dynamically to changes in folder permissions without disrupting workflows.
Key Benefits
1. Reduced Risk of Human Error
Automating the synchronization of permissions with data protection significantly reduces the likelihood of mistakes or oversights that could result in a data breach.
2. Eliminates Repetitive Manual Adjustments
The automation provided by SealPath federated policies removes the need for repeated manual input, enhancing operational hygiene and freeing up time.
3. Greater Operational Efficiency
By minimizing the effort required to manage permissions and protection, teams can shift their focus to higher-priority strategic initiatives instead of tackling administrative tasks.
4. Prevention of Conflicting Rules
Federated policies avoid overlapping or contradictory permissions, ensuring a streamlined and frictionless experience for employees while maintaining airtight security.
In conclusion, federated rules for protecting files in folders follow the principles of federated security applied to data access rights, thereby providing greater protection against data leaks and risks. Therefore, based on our experience of more than 10 years helping various entities protect their most sensitive data and information, we strongly recommend that organizations implement this practice.

